What is password less authentication?
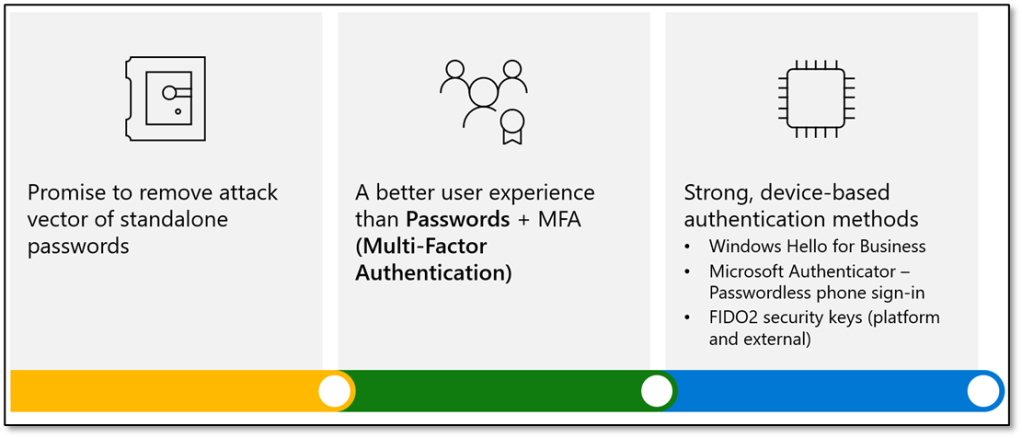
What is Microsoft’s Password less strategy?

There have recently been an increased amount of brute force password spray attacks against M365 \ Azure AD tenants.
The obvious protection is to implement (MFA) Multi Factor Authentication as the first line of defence.
A complex 8 character password that is not protected with MFA can be cracked in 24 hours or less.
I recently worked on a project where some M365 user accounts were brute force password sprayed attacked over 20,0000 times in a single month.
A lot of organisations make the mistake of having a ‘Meet the Team’ section on their corporate website, including the senior team member’s email addresses, which is one of the first places a bad actor will target.
Bruce force password spray attacks are not performed by human beings, they are performed by bots, hosted on private cloud networks or some public cloud networks……
A simple solution to protect an organisation against brute force password spray attacks is to enable Microsoft password less, gps authentication and biometric authentication via the Microsoft Authenticator application.
Conditional access policies that allow or block countries are not effective as a bad actor can simply mask their IP and pick any country code IP that they choose.
Microsoft password less authentication methods
Microsoft Authenticator
FIDO2-compliant security keys
Windows Hello for Business
Microsoft password less methods wizard
Microsoft Authenticator password less authentication mechanism
To enable password less and GPS location authentication , please implement and test the following configuration.
1. Browse to Azure Active Directory\ Security \ Authentication Methods
2. Select Microsoft Authenticator
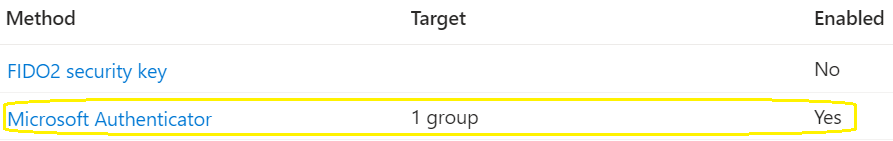
3. Enable and target a test group before enabling the feature for all users
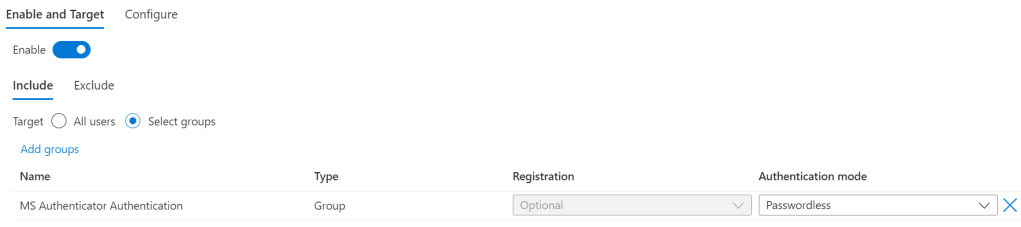
4. Select the following 3 configurations


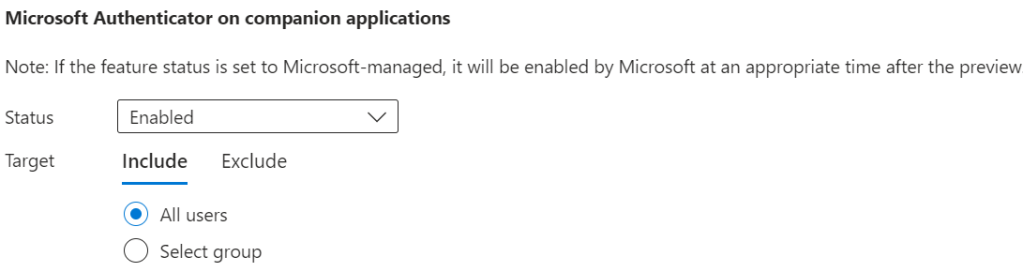
Microsoft Authenticator Application Configuration
The end user must enable phone sign in on the Microsoft Authenticator application. Currently, this can only be enabled for one password less account on Android, but multiple accounts on iOS.

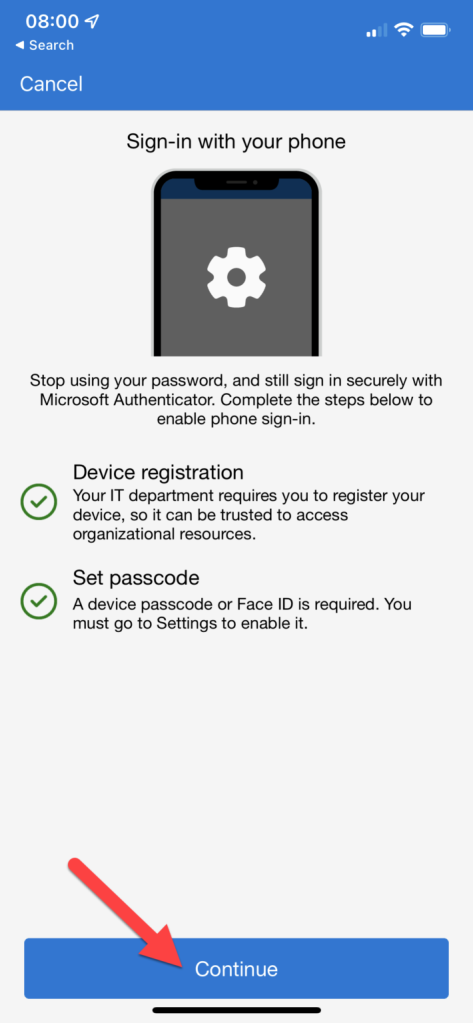
End User Experience

No password

Click yes if you are in Dublin, no if the GPS notification is displaying an incorrect location. The GPS location, protection mechanism must be communicated to end users. Do not click yes if the GPS co-ordinates specifies Hong Kong, if you are in Dublin

The final step is to validate via biometric thumbprint on your Android or iOS device.
Summary
Brute force password spray attacks cannot succeed when the following authentication methods are in place.
1: Password less
2: GPS verification
3: Biometrics validation on the Microsoft Authenticator application
The end user experience is much more user friendly, and most importantly a lot more secure.