This blog post will focus on the triggers and actions available in the ‘Microsoft Defender ATP API’ and how Power Automate can, automate tasks using this API.
The number 1, recommendation is to use Microsoft Sentinel. In my view SIEM without SOAR is useless.
When can an organisation be truly ready to enable SOAR automation for Windows 10\11 endpoints?
The Microsoft portal security.microsoft.com/Vulnerability Management/recommendations section provides recommendations on all endpoint vulnerabilities.
How does this section of the Microsoft security portal, provide recommendations on devices that have not been enrolled into Microsoft Defender for Endpoint management? This can be controlled via the Microsoft security portal device discovery configurations.
Typically organisations do not transition, straight away to using (MEM) Microsoft Endpoint Manager to provide software update services.
A remediation task in MEM to update a version of Google Chrome or Notepad ++, can only be actioned if, MEM is controlling software updates and if the latest versions of Google Chrome or Notepad ++ are available in the MEM Microsoft Windows application repository for Windows 10\11 devices.
I recommend that an organisation, responds to all security.microsoft.com/Vulnerability Management/recommendations, via their existing software update service prior to transferring update services to MEM. MEM provides excellent automated software update services to Microsoft software products, but can be quite cumbersome when it comes to updating 3rd party software products, like Google Chrome and Notepad ++
Some organisations, make the mistake, and think that enabling (MDFE) Microsoft Defender for Endpoint – auto remediation, will just work and protects endpoints from all threats.
The Microsoft ‘Defender Vulnerability Management add-on license‘, provides the ability to create some of the following, security baseline assessments.

Run these baselines , my preference is the CIS security baseline and improve the security posture of an organisation’s Windows 10\11 devices as much as possible before implementing, Microsoft Defender for Endpoint – Auto Remediation, or Microsoft Defender automation tasks via Power Automate or Microsoft Sentinel.
The Microsoft : security.microsoft.com portal provides a service called ‘Custom detection rules’, however the frequency of ‘custom detection rules’ is ‘every hour’, which is not good enough.
Power Automate – automated protection via the ‘Microsoft Defender ATP API’
Firstly, there are two amazing blog posts that describe the process of using Power Automate on how to auto isolate, Windows 10\11 devices, based on their severity risk level.
Nächster Artikel : extending-mdatp-alerting-sending-text-messages-sms-and-push-notifications
Ammar Hasayen: MS Flow and MS Defender ATP Integration
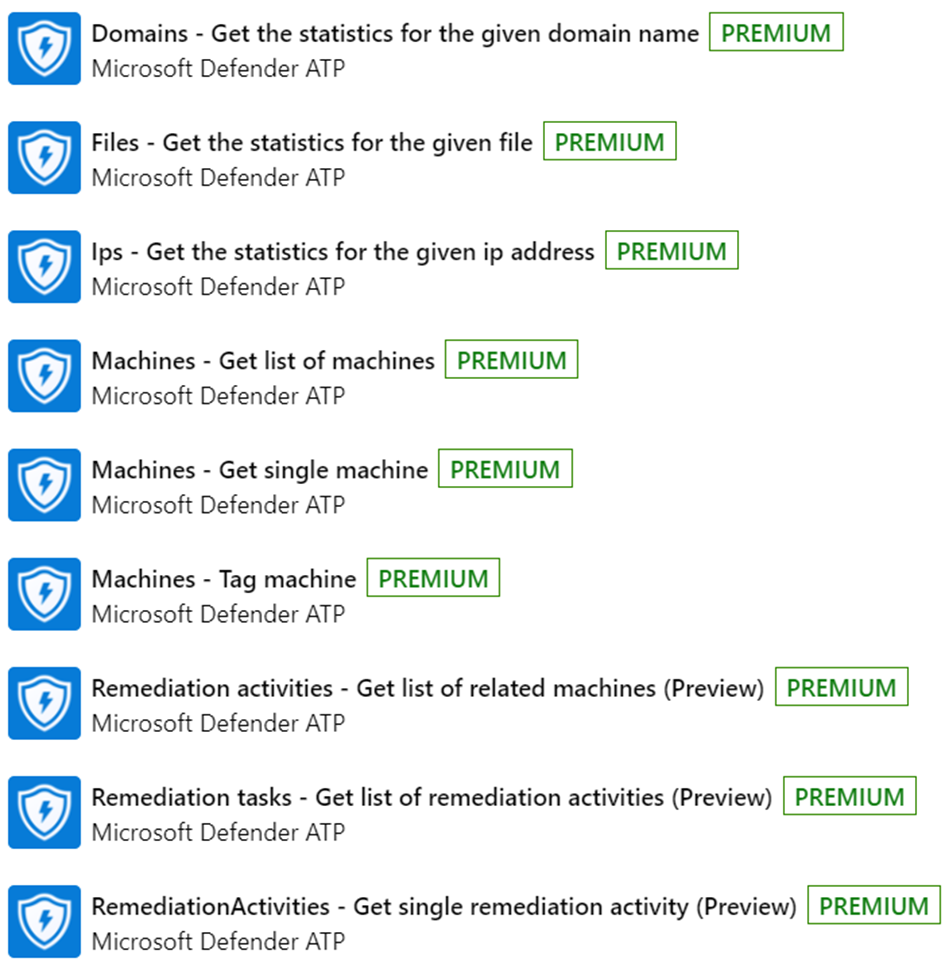
Microsoft Defender ATP API’ Triggers

‘Microsoft Defender ATP API’ Actions
The following actions, clearly illustrate the power of the ‘Microsoft Defender ATP API’, when an organisation has improved their security posture with Windows 10\11 devices. With some Power Automate or Microsoft Sentinel runbooks, these actions can enable an organisation to protect a bespoke line of business work flow on endpoint devices.
Some organisations may say, ‘Why MDFE, cannot, just provide this protection as standard’, and the simple answer is, every organisation’s line of business applications or workflows are different and require, custom, granular control, that the ‘Microsoft Defender ATP API’ can provide via Power Automate but, most preferably : Microsoft Sentinel.
The following images outline the actions that are possible using the ‘Microsoft Defender ATP API’



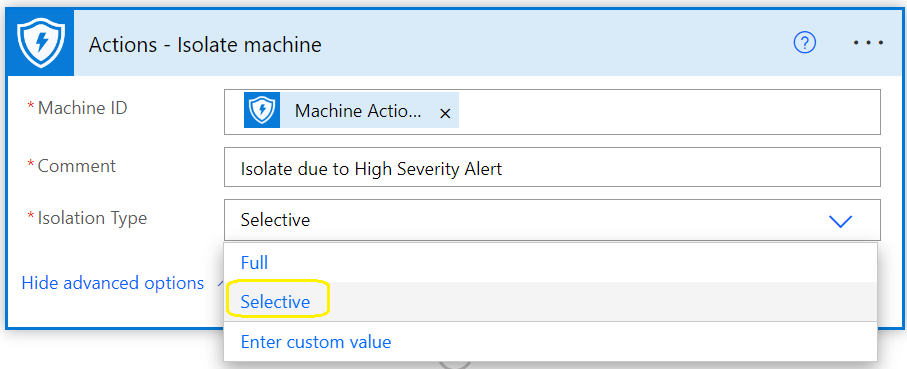
Microsoft Defender Auto Isolation new Feature
It is now possible to ‘isolate’ devices but continue to allow end users to use ‘Microsoft Outlook and Teams’
This feature, ensures that end users can continue to remain productive in their daily work routines when using Windows 10\11 devices, yet be isolated from their corporate network, probably the best use case, is to prevent the spread of ransomware or Mimikatz credential theft.
How is this Auto Isolation feature to allow users to continue using ‘Microsoft Outlook and Teams’ controlled in the ‘Microsoft Defender ATP API’