Microsoft’s unwavering commitment to security and compliance has consistently driven innovation and adaptability to meet evolving industry demands. Their dedicated security and compliance portals have left the legacy portal, portal.office.com, in the not too distant past.
One common frustration for M365 administrators is the inability to assign the following roles within Microsoft Privileged Identity Management:
- Microsoft Purview roles’
- Microsoft Defender roles’
- Microsoft Dynamic roles’
This blog post will primarily delve into the assignment of Microsoft Purview roles. The image below showcases the default role assignment choices available in Microsoft Privileged Identity Management.

Microsoft Purview Roles
Microsoft has invested significantly in their portal redesign at compliance.microsoft.com. In traditional scenarios, IT administrators often find themselves tasked with configuring, executing, exporting e-discovery case results, and subsequently reporting to compliance officers, data protection officers, or HR departments. However, entrusting IT admins with these compliance tasks raises initial concerns about data protection. It’s imperative that IT admins remain unaware of sensitive information contained within e-discovery case results, as these results might encompass IT admin staff within the search criteria.
As of the time of this post, there are approximately 95 role groups within M365 Purview. Here are some practical use cases illustrating how these roles can be assigned to fulfil various compliance roles and organizational requirements:
- e-discovery
- Insider Risk Management
- Privacy Management
- Data Investigator
How to Assign Microsoft Purview Roles to Microsoft Entra ID Groups
Note: For the purposed of this blogpost, I created a Microsoft CDX tenant, all users and screenshots are fictional.
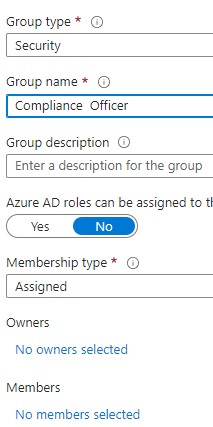
1: Create a Microsoft Entra id group. Important, to not add any members or owners
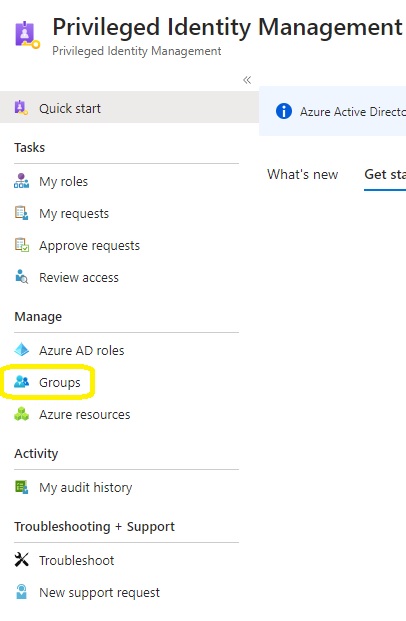
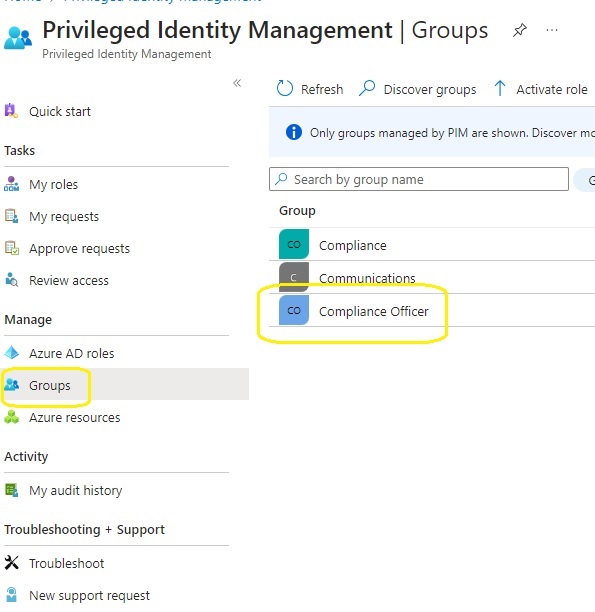
2: Login to Microsoft Entra Privileged Identity Management and select Groups.
3.Seclect Discover Groups

4.Search for the previously created group and then select manage groups
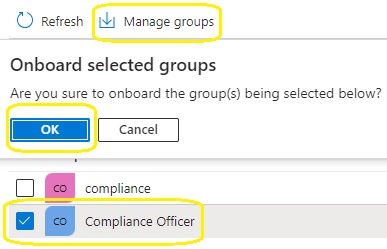
5.Select groups in Privileged Identity Management

6. Click on assignment, add members to eligible assignments, this is why , we did not need to add any group members in step 1
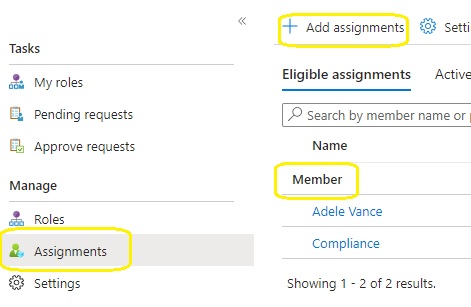
7. Click on settings and member

8. Edit the member settings

9. Set hours to 4, require justification on activation, require approval to activate and then finally select the approver. The approver may be different per role that requires activation.

10. Create a role group in the compliance.microsoft.com portal : Microsoft Purview Permissions
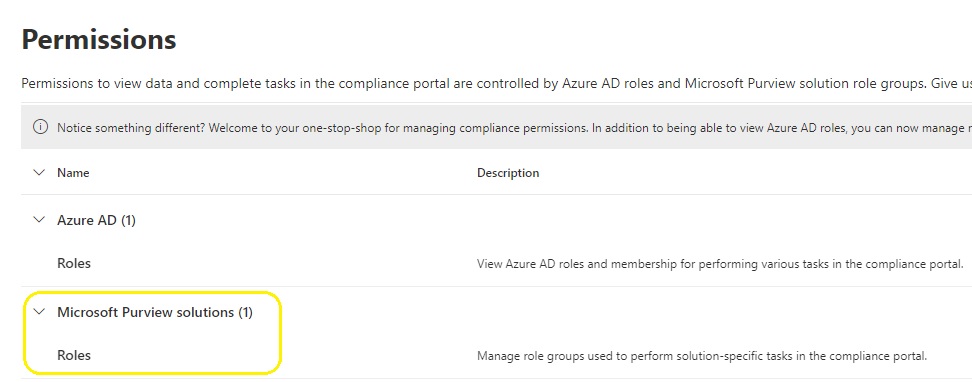
11. Name the role group

12. Add the roles.
Select all roles
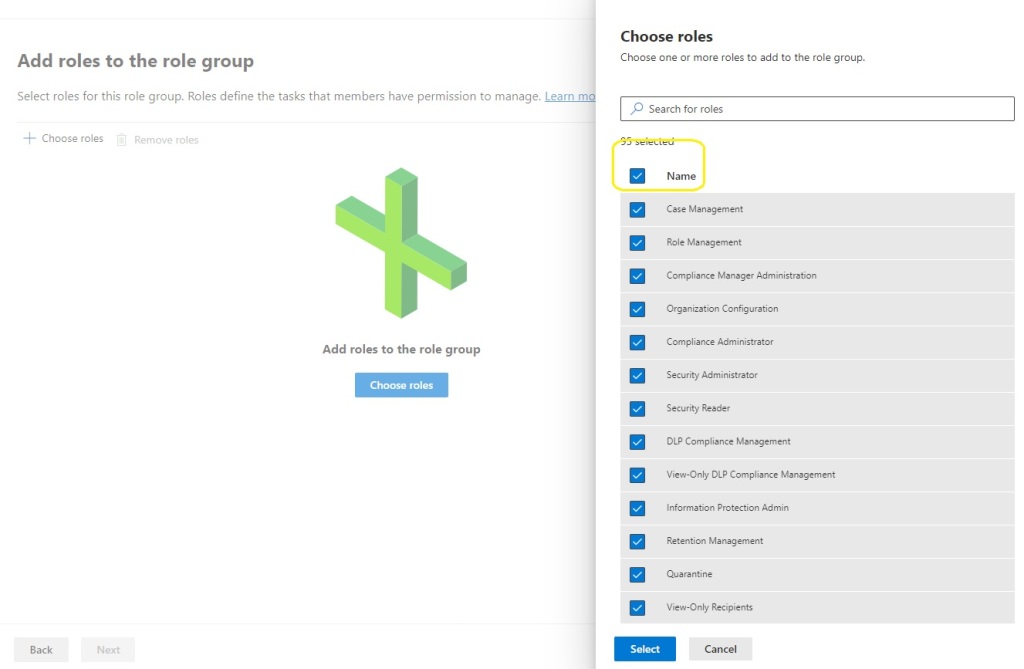
13. Choose groups and add the group that was created previously

14. Now the end user Adele Vance can login to https://entra.microsoft.com /identity governance / Privileged Identity Management and select ‘Activate just in time’
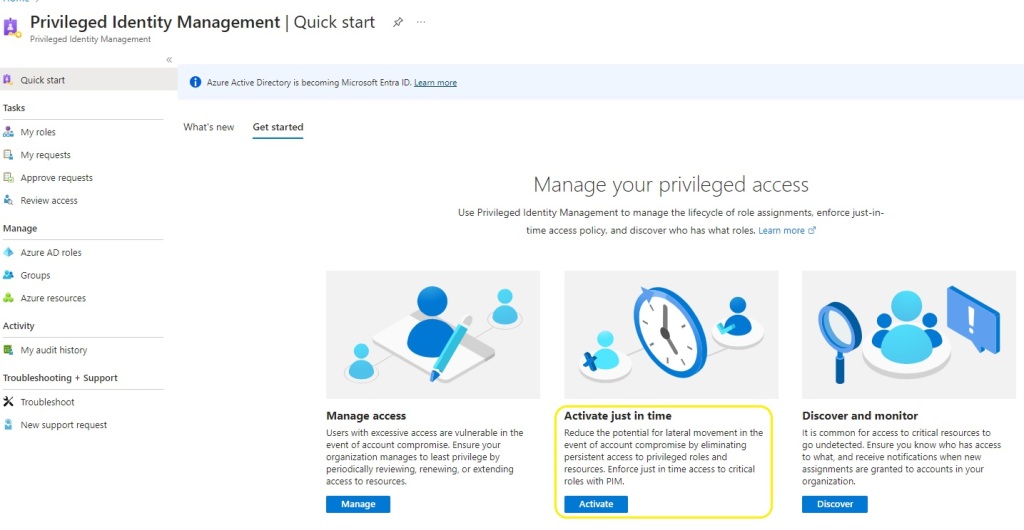
15. The user then selects group, activate and provides a business justification.
16. The group owner and admin , receives an email notification, that there is a pending just in time access request and can choose to approve or deny the request.
17. The compliance officer can then login to complicane.microsoft.com and perform his\her compliance activities. During my testing, no license was required for the compliance officer. I am sure Microsoft would insist that the compliance officer has an M365 E5 or E5 compliance add-on license:)
Summary
The technical steps outlined in this blogpost, enable organisations to apply Privileged Identity Management policies to roles \ permissions control in services like
- Microsoft Purview roles’
- Microsoft Defender roles’
- Microsoft Dynamic roles’
M365 Purview roles are not available in M365 roles or Microsoft Entra ID Privileged Identity Management, for really good reasons. M365 Purview role \ permission elevation , can be typically required for legal disputes.
Every organisation, should consider compliance and governance with a cloud transformation journey where services, data and line of business workflows, transition from on-premises to Microsoft cloud services.
If anyone, or any organisation would like some further assistance with this, please get in touch with me via LinkedIn : https://www.linkedin.com/in/seanofarrelll/