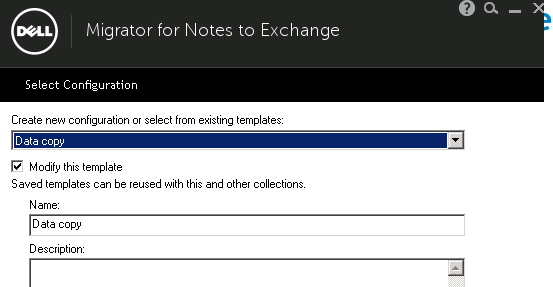
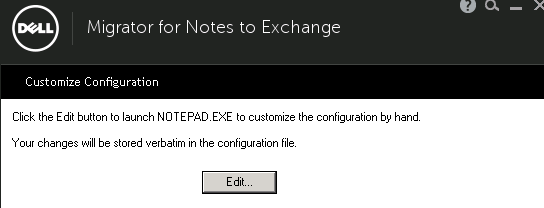
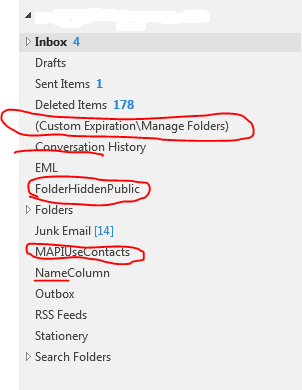
When using templates in Dell MFNE 4.1 , The template does not read the global settings defined in the tool.
Category Archives: Uncategorized
Bulk Uploading Mailboxes to Exchange Online and assigning licenses
Replacing TMG with IIS ARR for an Exchange Hybrid
The Exchange Team Blog have a three part article on how to set it up and install it
Part 1 , Part 2 , Part 3
- /ews/mrsproxy.svc
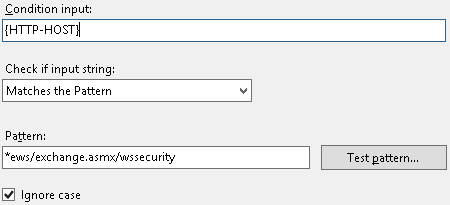
- /ews/exchange.asmx/wssecurity
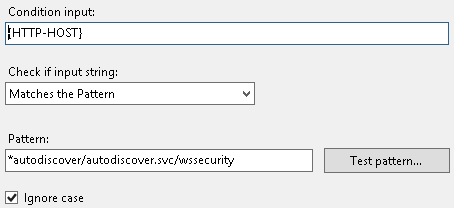
- /autodiscover/autodiscover.svc/wssecurity
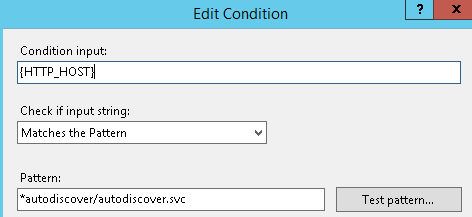
- /autodiscover/autodiscover.svc
Converting Office365 Cloud Identities into Managed Identities
There are three core identity scenarios in Office365 as illustrated above. I created a previous blog post on how to covert cloud identities to federated identities which can be viewed HERE
To convert cloud identities to managed identities with password sync can be quite simple by changing the users UPN and also matching the user’s UPN with their primary smtp address.
However , How many time have you received the dreaded email from Microsoft like below
| Sean Ofarrell |
Unable to update this object because the following attributes associated with this object have values that may already be associated with another object in your local directory services: [ProxyAddresses SMTP:sean.ofarrell@contoso.com]. Correct or remove the duplicate values in your local directory. Please refer to http://support.microsoft.com/kb/2647098 for more information on identifying objects with duplicate attribute values. |
Using Azure RMS with Office365
How to update Exchange Online and Office2013 users so that they can receive new custom templates.
Azure RMS Sharing Application
FAQ for Microsoft Rights Management Sharing Application for Mobile Platforms
How to perform WAAD Manual Sync
WAAD version 4.3.647.0 seems to have moved the powershell module for manual syncs. To put the shortcut back on the desktop of your WAAD Server. Simply create a new shortcut and paste in the details below and then type start-onlinecoexistencesync to perform a manual sync
powershell.exe -noexit -noprofile -file “C:\Program Files\Windows Azure Active Directory Sync\DirSync\ImportModules.ps1”
How to enable Yammer SSO without ADFS
- Browse to the Active Directory section in the Azure Management Portal and then select
“Add Application” and “Add an application my organization is developing”
as per the image below.
- Name your application as per image below
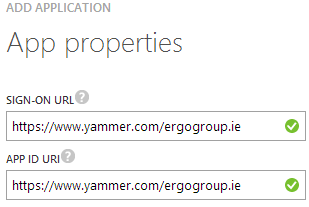
- Then enter your sign-on url & app id uri as per image below
- You then select “ENABLE USERS TO SIGN ON” and then browse to the “FEDERATION METADATA DOCUMENT URL” and save the metadata xml file as per image below.
- Next we need to connect Windows Azure Active Directory via powershell and run the following commands
- The command will output an “AppPrincipalId” take note of this value and save it into a text file.
- Then you will need to fill in the Yammer SSO-Checklist.docx which you can download HERE
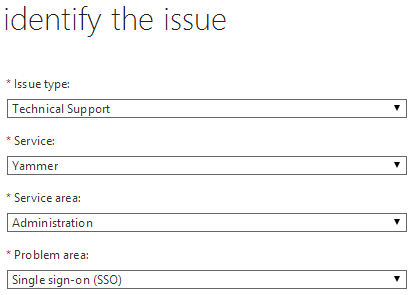
- We now create a Service Request as per image below
- We then create a compressed file that contains the FederationMetadata.xml, the AppprincipalId and the SSO Checklist and attach the file to the service request.
Cloud Accelerate Partner Support
One of the benefits of being a Microsoft Cloud Accelerate Partner is that you can get dedicated Cloud Partner Support which is available 24 Hours a day 7 days a week.
So how do you access this benefit as there is no dedicated phone number.
The way you access the Cloud Partner Support team is by logging a service request via your partner tenant. So you can log a service request through your own partner tenant for one of your customer’s tenants.
This really is an excellent service. Its like having a Microsoft Premier Support contract. I have logged a number of service requests via the Cloud Partner Support team and their response time is excellent.
HERE is a document providing an overview of the Cloud Deployment Program Overview
QUEST NME unable to create admin pool
In the image above I ran into an issue when trying to create an admin pool for on Quest Notes For Exchange migration toolkit.This was for a migration to Exchange Online.
So the first thing i did was set-executionpolicy unrestricted -force on both the x64 and x32 versions of powershell. But that didn’t fix the issue.
Most enterprises have quite a few group policies and sometimes these policies are applied before the machines have been moved to an OU that has inheritance blocked.
So to remove the group policies causing the issue.